Welcome!
If you’d like to jump straight in and start using Reaper, check out the Getting Started guide to get up and running quickly. Otherwise, read on for more information about Reaper.
What is Reaper?
Reaper is a reconnaissance and attack proxy, built to be a modern, lightweight, and efficient equivalent to Burp Suite/ZAP etc. This is an attack proxy with a heavy focus on automation, collaboration, and building universally distributable workflows.
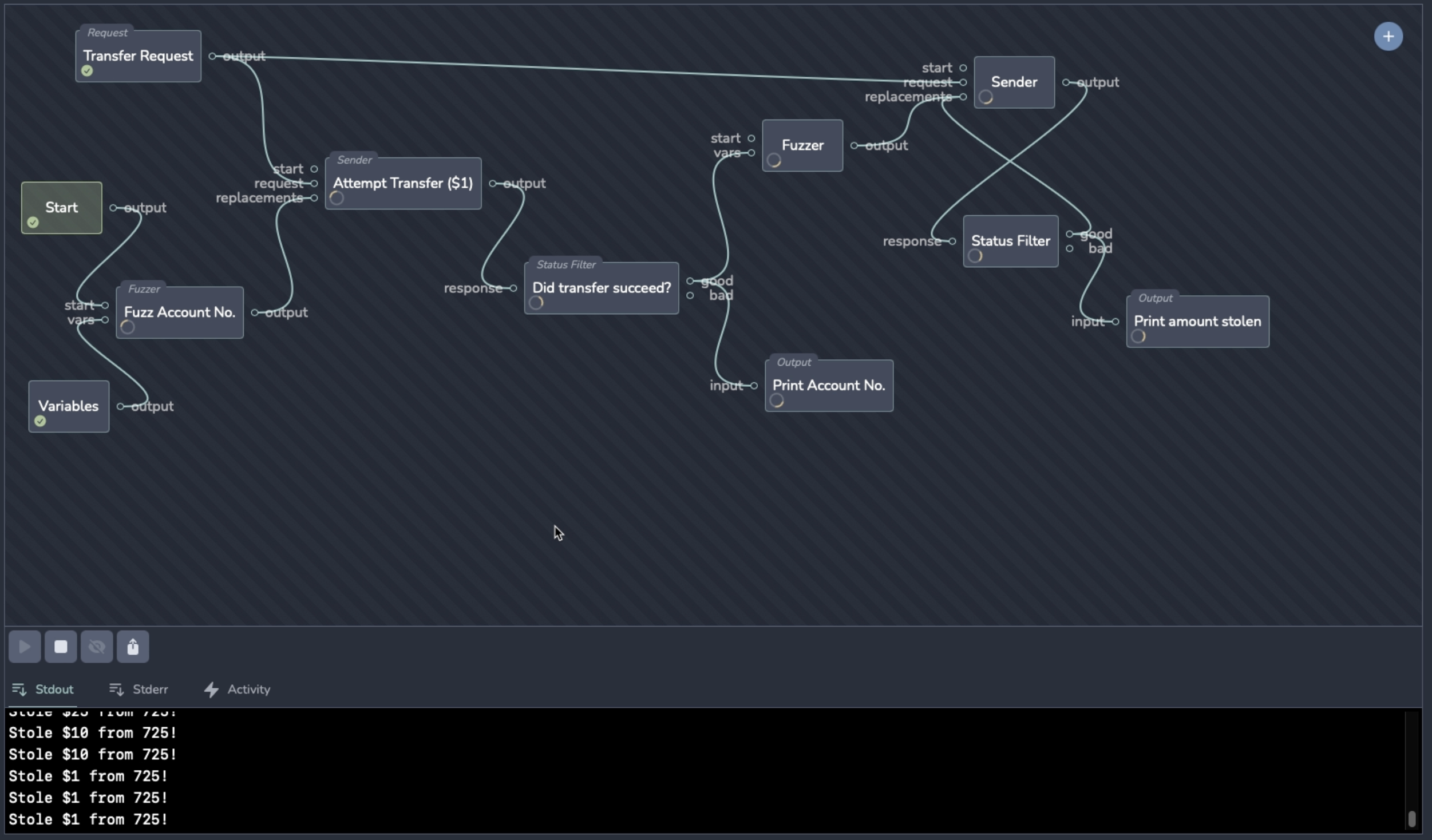
What can I do with Reaper?
Reaper is a work in progress, but it’s already capable of a lot. Here’s a quick overview of some things you can do:
- Intercept and modify HTTP requests and responses
- Save and categorise HTTP requests/responses for later examination/reuse
- Manage multiple projects and project-specific settings using workspaces
- Incrementally craft workflows to attack web applications using our unique GUI
- Automate simple tasks like fuzzing, brute-forcing etc.
- Perform automated attacks against web applications
- Create, share and collaborate on custom workflows to automate your testing
Who builds Reaper?
Reaper is built by Ghost, a global team of security professionals, researchers, and hackers; and you!